Proxy Server: What Is It & Why People Use It? Is VPN Better than Proxy?

Get to know better on what is a proxy server, what’s it used for, how to configure it and VPN vs. proxy details.
From tech posts, forum discussions, or the internet settings of various machines and apps, you may come across the words “proxy” or “proxy server” but have no clue on what is it, why you need it and what to choose between proxies and even VPNs in different situations. To figure everything out and help beginners understand proxy server better, this post just comes in to explain it in an easy way.

What’s the Meaning of Proxy (Server)? Definition
In the computing network, the proxy actually refers to the proxy server which can be a system or a router and serves as an intermediary between the server offering resource and user client asking for the resource. Some also take the proxy servers as the gateways between end user and the internet, like when browsing a website, accessing an email server, or a local data center.
Proxy services are often used for security, privacy, performance optimization, or content (un-)blocking benefits. Sometimes it acts like the VPN. When it re-routes the internet traffic, the originating IP address from the device that makes resource requesting will be hided, thus you can be anonymous and the target server only sees another new IP address from the proxy server.
How Does a Proxy Server Work?
Since being a server-in-the-middle, the proxy will forward any web request and have the traffic flow through its server first before arriving at the destination just like the following workflow picture shows:
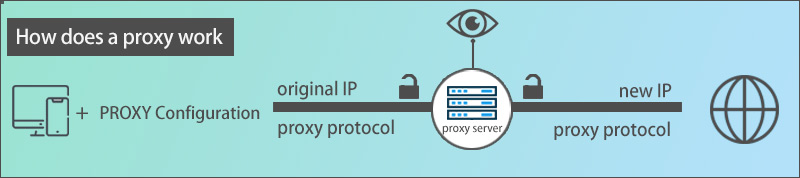
Obviously, if you have already configured the proxy up on your device via a standalone proxy app client, app-, system- or router-based proxy settings when you are making a web request, the request will first reach the proxy server and then be sent to the destination.
When the destination delivers feedback/response to the request, it’s the proxy server that receives the response and forwards it back to you again. During this process, your original IP address will be hided and what the target server sees is the IP from the proxy server.
But since the security level, speed, and features of a proxy may vary from service, it’s hard to draw a conclusion on whether it’s safe, efficient, or not. If you are using a proxy with no encryption, your browsing history, and other personal information may be recorded or stolen from proxy server providers, governments, advertisers, and hackers easily. Now let’s take a look at some typical proxy names.
Related articles: How does a VPN work
Some Proxy Types Shared
Also, there are many types of proxy servers to meet various user demands, and we just list some typical ones according to their agreements, workflows, security level, and so forth.
| Main Types of Proxy Servers | |
| Classification criteria | Proxy server names |
| Proxy protocol | HTTPS (SSL/TLS) proxy, HTTP proxy, Socks proxy, FTP proxy, Telnet proxy, RTSP proxy, POP3/SMTP proxy, DHCP (Relay) proxy…. |
| User access rights | Open proxy, Closed proxy |
| How it works | Forward proxy, Reverse proxy |
| OSI model | Application-layer proxy, Transport-layer proxy, Network-layer proxy |
| Workplace | Hardware proxy, Software proxy |
| Number of user(s) | Shared proxy, Dedicated/Private proxy |
| Anonymity | Anonymous proxy, High Anonymous Proxy |
| Security | Transparent proxy, Non-transparent proxy |
| IP source | Residential proxy (Static/Rotating proxy server), Data-center proxy |
| How to use it | Web proxy server, |
| What’s used for | Education Network proxy, SSO proxy, Flat proxy, Distorting proxy, Smart DNS Proxy Server… |
The meaning of several most commonly used proxy servers are given for your reference:
– Anonymous Proxy is a mainstream proxy type that only works on behalf of the user but will not reveal the user’s IP address so that your online identity and browsing history can be shielded. This way, you can stay away from those annoying targeted ads. However, the anonymous proxy server itself can be detected, which means the requested web server knows the request is from a proxy server. Another high anonymous proxy, just as the name shows, provides better anonymity by renewing IP addresses to users as long as any old ones are added into the IP blacklist by others.
– Transparent proxy offers identity protection for both itself and the your device’s IP address. So compared to anonymous proxy, although they both belong to open proxy, transparent proxy is suggested to use for full anonymity. Also, it features caching a website hence you can enjoy a faster retrieval if the site you visit was visited and cached before. But this proxy server is not recommended for users who care the security.

– Public proxies are the free ones that all people can access and use to hide IP address at no cost. Definitely, those free proxy servers on the web are all public proxies. And under these circumstances, when many users work with the same proxy, then this is also called shared proxy. Chances are if too many users are using the same shared/public proxy, it will affect the speed greatly.
– To obtain the proxy and IP addresses by yourself only, you are free to employ a dedicated proxy (aka private proxy) to enjoy its perfect performance and reliable security.
– Forward Proxies that are run with clients are widely used in companies and organizations to permit a certain group of people to access their internal networks for any possible purposes. The proxy server offers administrative settings to allow or deny any access request for end-users. Note that the proxy servers average customers use is actually the forward proxy servers.
– Speaking of the forward proxies, we have to come up with another proxy named reverse proxy. In contrast with forward proxies, reverse proxy (web) servers work on behalf of the server and hide their identities. More often, it’s taken as a solution to load balancing, caching, server security, and so forth.
– A residential proxy not only enables the IP concealing, but also authorizes you to use the IP address from real ISP on a fixed device and physical location just like a native user. Nevertheless, another datacenter proxy doesn’t have affiliate relationship with and give IP address from the ISP but some other corporations. People can still gain benefit of it, become anonymous online and override internet content filtering for better web privacy and freedom.
– SOCKS proxy servers can be divided into SOCKS4 and SOCKS5 proxies, among which SOCKS5 is more popular thanks to the support for both TCP and UDP while SOCKS4 proxy servers only support TCP.
– Users often use HTTP proxies to visit general web pages, SSL/HTTPS proxies to access the encrypted sites and SOCKS5 proxies for any forms of web behaviors.
Both employers and individuals are free to choose what kind of proxy server to use for (remote) work and daily life according to their real demands.
Benefits of Proxy Server Usage
For ordinary beginners, what comes to ones head to utilize a proxy is to alter IP address to secure digital privacy and unblock some restricted sites or services just like Netflix (>>see how to unblock Netflix guide). As a matter of fact, the proxy servers are able to do more things than you may think. Below are some main reasons to apply a proxy are listed.

– Enhance users’ online security and privacy by masking the real IP address and preventing IP-based tracking.
– Circumvent various content blocking to access blocked sites, social apps, streaming libraries, and many more without hassle.
– Regain the ability to join the forums, communities and similar places that block your IP or take you as a spammer.
– Control what employees can do and monitor their activities during working hours, to guarantee security and efficiency.
– Balance internet traffic to avoid unexpected crashes.
– Cache resources and save bandwidth for a faster connection next time.
…
Proxy Server vs. VPN, What’s the Difference and Who’s Better?
For normal users, whenever there’s a willingness to get a proxy server, there’s a chance to be informed to take the VPN option into consideration. That makes the comparison between the proxy server and VPN a necessary thing to learn.
Simply put, they two are both capable of hiding your IP address and help you go further with those banned web content. Nonetheless, the key difference lies in that VPNs can encrypt your connection since it works with VPN protocol and unique tunneling tech while proxy servers are more likely to be pure gateways to resolve content blocking issues basically, without necessarily extra data encryption.
So it’s easy to draw that a VPN is superior to a proxy in most cases, especially for people who value their personal data, who handle sensitive materials, and who are willing to obtain a higher level of web privacy. Here we suggest you get simple, fast yet safe PandaVPN to meet any needs for owning a proxy.
PandaVPN currently has over 3000 servers in 80 countries and 170 locations worldwide. With first-in-class protocols and encryption algorithm embedded, you are free to connect to anyone to become invisible & untraceable, to bypass geo-blocking, to carry out special missions and view banned resources secretly.
FAQs
1. Are Free Proxy Servers Safe to Use?
As mentioned above, these free proxies you come across online are public shared proxies. On one hand, they may provide slow connection speed which is hard for watching (4K/1080p) streaming files. On the other hand, freebies may keep your logs for profit or other purposes. Hence, free proxies are not recommended to use unless you just want a tool for IP concealing or accessing prohibited pages and don’t mind your privacy.
2. How to Choose a Proxy Server?
To pick a suitable proxy, you’d better make your requirements clear in advance and then confirm what type of proxy is more proper. Then, do check top-ranked proxy server providers and user reviews from big review sites or so to narrow the choices down. At last, select the one within your budget.
3. Is a VPN a proxy?
No. Although the workflow of a VPN is similar to that of a proxy, they are two different things. However, since certain VPNs may have support for proxy protocols like Shadowsocks, when it runs with the proxy protocol, the VPN can be regarded as a proxy.
 Vic Knott
Vic Knott  2022.04.08
2022.04.08 











